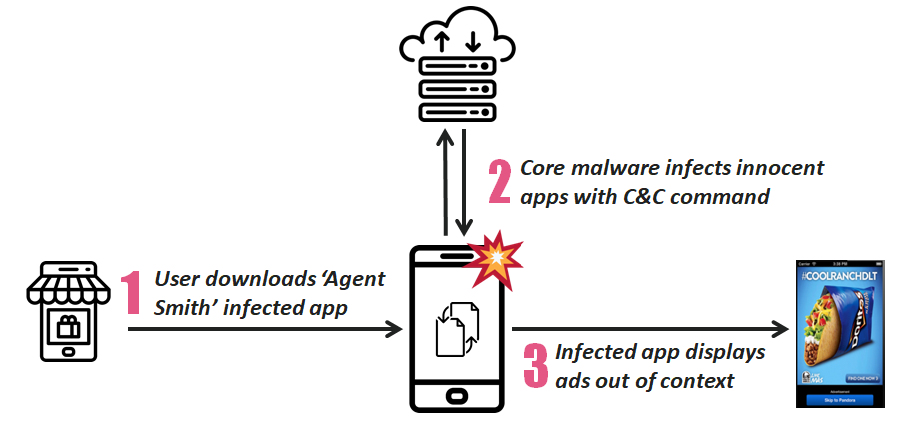
New variant of mobile malware has infected around 25 million devices, in which 15 million are from India, according to cyber security firm Check Point‘s research report. Malware Agent Smith auto replaces already installed apps with malicious version without any user initiation completely silently, users have no idea of this app replacement. This unique on-device, just-in-time (JIT) approach inspired researchers to dub this malware as “Agent Smith”.
It disguised as Google normal apps, mobile malware exploits various known Android devices vulnerabilities and automatically replaces installed apps on the device with malicious versions without the user’s interaction.
Malware Agent Smith broadly using its access to the mobile devices as a resources to show fraudulent, spam ads for financial gain, but could easily be used for far more intrusive and harmful purposes such as financial banking login credential theft and eavesdropping. This activity resembles previous malware campaigns such as Gooligan, Hummingbad and CopyCat.
Mobile malware Agent Smith Attack flow
Head of Mobile Threat Detection Research at Check Point Software Technologies, Jonathan Shimonovich said “The malware attacks user-installed applications silently, making it challenging for common Android users to combat such threats on their own, Combining advanced threat prevention and threat intelligence while adopting a ‘hygiene first’ approach to safeguard digital assets is the best protection against invasive mobile malware attacks like “Agent Smith”. In addition, users should only be downloading apps from trusted app stores to mitigate the risk of infection as third party app stores often lack the security measures required to block adware loaded apps.”
Malware Agent Smith was originally downloaded from the widely-used third party app store, 9Apps and targeted mostly Hindi, Arabic, Russian, Indonesian speaking users. So far, the primary victims are based in India, approx 15 million devices infected with this mobile malware, Pakistan and Bangladesh devices also have been targeted and infected.
There has also been a noticeable number of infected devices in the United Kingdom, Australia and the United States. Check Point has worked closely with Google and at the time of publishing, no malicious apps remain on the Play Store.
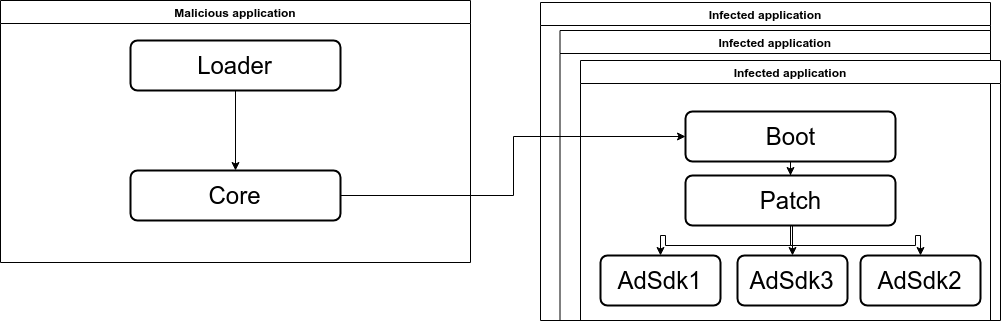
Agent Smith malware has a modular structure and consists of the following modules:
- Loader
- Core
- Boot
- Patch
- AdSDK
- Updater
As stated above, the first step of this infection chain is the dropper. The dropper is a repacked legitimate application which contains an additional piece of code – “loader”.
The loader has a very simple purpose, extract and run the “core” module of “Agent Smith”. The “core” module communicates with the C&C server, receiving the predetermined list of popular apps to scan the device for. If any application from that list was found, it utilizes the Janus vulnerability to inject the “boot” module into the repacked application. After the next run of the infected application, the “boot” module will run the “patch” module, which hooks the methods from known ad SDKs to its own implementation.